Welcome Back
Last month, we continued our unfiltered dive into the dark web by explaining the basics and diving into some general finds. If you missed Part 1 or 2, you can now access them on our website.
Before we start, we want to reiterate that playing around on the dark web can have serious repercussions. Given its daunting and enigmatic reputation, most people have never ventured out to see what really exists on the dark web. We'll give you a peek behind the curtain so that you don't have to put yourself at risk!
SEVN-X does not endorse or condone any material or activities mentioned in this article, nor does it seek to provide commentary or regard with bias any of the sites, users, or material depicted. Screenshots are included for educational purposes only.
Welcome to the Black Market
The last installment of our Dark Web Exposed series focused on entry level findings. It's time we dive into the darker side of the dark web and expose nefarious findings. We must give a disclaimer however as there are sinister applications on the dark web that we are not willing to touch on... use your imagination.
Things take a more sinister turn when we encounter a Black Market site. Here, one can purchase fake or stolen IDs, passports, and credit cards for as little as $60!
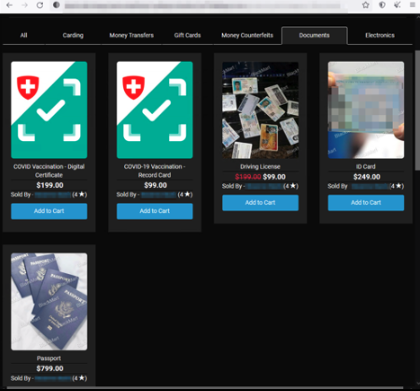 Black Market Sales Items
Black Market Sales Items
Breached Database Dumps?
Breached database dumps are sold in bulk and on a per-record basis on this site. When a threat actor breaches a network and exfiltrates data, that data frequently appears on dark web markets such as this, available for a price.
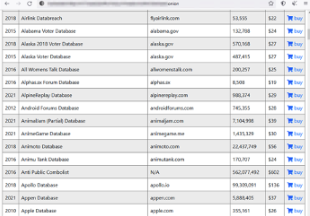 Database Dumps
Database Dumps
In some cases, stolen data is published freely for all to see.

or
 Stolen Data Free to Use
Stolen Data Free to Use
When data is exfiltrated, there is no way to contain its spread. Once it becomes available on the dark web, there is no telling who might get their hands on it and what they might do with it. The best measures an organization can take to safeguard against this risk is to prevent the data exfiltration from happening in the first place. Network monitoring solutions, privileged account management, and regular security assessments, such as penetration tests and vulnerability scans, are high-impact actions an organization can take to mitigate this risk.
At SEVN-X we're dedicated to helping create those safeguards so that you don't ever have to be a dark web statistic. If you have any questions about the services we provide or if you think that you are't as secure as you should be, then don't hesitate ... the bad guys aren't!
You can submit your information requests on our website.


Submit a comment